Table of Contents
The money conversion cycle (CCC) is just one of numerous procedures of management efficiency. It gauges just how fast a firm can convert cash money accessible into much more cash handy. The CCC does this by complying with the cash, or the resources investment, as it is initial converted into supply and accounts payable (AP), through sales and receivables (AR), and afterwards back into cash money.

A is the use of a zero-day manipulate to cause damages to or steal information from a system influenced by a susceptability. Software application often has safety and security susceptabilities that cyberpunks can manipulate to trigger havoc. Software application developers are constantly looking out for susceptabilities to "patch" that is, establish a service that they launch in a brand-new upgrade.
While the vulnerability is still open, assailants can write and carry out a code to take benefit of it. Once assaulters determine a zero-day susceptability, they need a means of getting to the susceptible system.
The 7-Second Trick For Security Consultants
Safety and security vulnerabilities are often not uncovered right away. In recent years, cyberpunks have actually been quicker at manipulating vulnerabilities quickly after exploration.
: hackers whose inspiration is typically financial gain cyberpunks encouraged by a political or social cause who desire the attacks to be visible to draw interest to their reason hackers that spy on business to gain details concerning them countries or political stars snooping on or striking one more nation's cyberinfrastructure A zero-day hack can exploit susceptabilities in a variety of systems, consisting of: As an outcome, there is a wide array of potential sufferers: People that make use of an at risk system, such as a browser or running system Hackers can use safety and security vulnerabilities to compromise tools and build huge botnets People with accessibility to useful organization information, such as copyright Hardware gadgets, firmware, and the Web of Points Large services and organizations Federal government firms Political targets and/or nationwide protection threats It's useful to assume in regards to targeted versus non-targeted zero-day attacks: Targeted zero-day attacks are performed versus possibly important targets such as large organizations, government companies, or high-profile individuals.

This website makes use of cookies to help personalise web content, tailor your experience and to maintain you visited if you register. By continuing to utilize this site, you are consenting to our use cookies.
The smart Trick of Security Consultants That Nobody is Discussing
Sixty days later on is normally when a proof of concept arises and by 120 days later, the vulnerability will be consisted of in automated vulnerability and exploitation devices.
Before that, I was simply a UNIX admin. I was thinking of this inquiry a whole lot, and what took place to me is that I do not know too numerous individuals in infosec that chose infosec as an occupation. Most of individuals who I understand in this field didn't most likely to university to be infosec pros, it simply sort of happened.
Are they interested in network security or application protection? You can get by in IDS and firewall program globe and system patching without understanding any kind of code; it's relatively automated things from the item side.
Things about Security Consultants
With equipment, it's a lot different from the work you do with software program safety and security. Infosec is a truly large space, and you're mosting likely to need to pick your particular niche, since no one is mosting likely to be able to bridge those gaps, a minimum of efficiently. So would certainly you claim hands-on experience is more vital that official protection education and learning and accreditations? The inquiry is are individuals being employed into entry level safety placements straight out of institution? I think rather, yet that's most likely still rather uncommon.
There are some, but we're most likely speaking in the hundreds. I believe the universities are recently within the last 3-5 years obtaining masters in computer system security sciences off the ground. There are not a great deal of pupils in them. What do you believe is one of the most crucial qualification to be effective in the safety and security room, no matter a person's background and experience degree? The ones who can code virtually always [fare] better.
And if you can understand code, you have a better likelihood of being able to comprehend exactly how to scale your option. On the defense side, we're out-manned and outgunned regularly. It's "us" versus "them," and I do not know how numerous of "them," there are, but there's going to be also few of "us "at all times.
Some Of Security Consultants
You can envision Facebook, I'm not certain several security individuals they have, butit's going to be a tiny portion of a percent of their user base, so they're going to have to figure out how to scale their services so they can protect all those customers.
The researchers discovered that without understanding a card number in advance, an assailant can launch a Boolean-based SQL shot with this area. Nonetheless, the database reacted with a 5 2nd hold-up when Boolean real statements (such as' or '1'='1) were provided, resulting in a time-based SQL injection vector. An assailant can use this trick to brute-force query the data source, permitting info from accessible tables to be exposed.
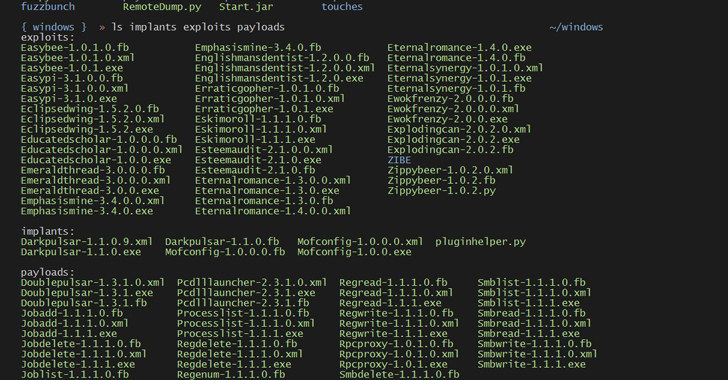
While the information on this dental implant are scarce at the moment, Odd, Task services Windows Web server 2003 Venture as much as Windows XP Professional. A few of the Windows ventures were also undetected on online file scanning service Infection, Total, Safety And Security Architect Kevin Beaumont verified using Twitter, which indicates that the devices have actually not been seen before.
Navigation
Latest Posts
Diy Plumbing around me Portland
Diy Plumbing close to Portland, Oregon
Diy Plumbing around me Portland, Oregon